How to Access Dark Web
In a world of ambiguity, we often desire to have things described in terms of black and white. If you are looking for such a book on the dark web, we must apologize. There is no way to paint the dark web as a truly evil construct (as popular culture often does) or as a perfect bastion of freedom (though we might like it to be considered that way). We instead wrote this book with the aim to tell the truth and to tell it in a way that any reader can understand. It is more important to us, as the authors, to help promote informed, democratic discussion than to convince you to side with our personal beliefs. If you come out of reading this book with greater knowledge and appreciation but still believe the dark web is an evil utility, our job is well done. If you come out of reading this book with greater knowledge, appreciation, and support for the dark web, then all the better.You will notice that this book spends relatively little time talking about the people who use the dark web—whistleblowers and the like. This is not a book to sing their praises—or to admonish them. We mention them enough to provide context, to understand who might use the dark web, but we are not so much concerned with convincing you Edward Snowden was right in what he did as with understanding why he did what he did and how he did it. Both of the authors of this book are trained as librarians, and the goal of librarians is to provide you with information—veracious facts—not to tell you how to use it. That’s up to you and you alone.
Download: Casting Light on the Dark Web the perfect book to browse safe
We will not hide the fact that illegal activities occur on the dark web. In fact, let us state here with clarity and authority that illegal activities absolutely occur on the dark web. However, that is only one side ofthe story. It’s the side ofthe story that draws clicks and brings in ad revenue, so undoubtedly it is the side you have heard far more about. But the dark web was not designed by terrorists or to be used for nefarious purposes. It was developed by the United States government to protect important communications from enemies. It was never intended for illegal uses. It was, in fact, intended for positive uses. That might sound like the good old Second Amendment debate in the US, but the arguments in this case are actually far clearer. We all know from our experience using the Internet that our privacy is not always held to the utmost standard.
Tor dark web browser
We guarantee that you all have had the same experience that first got the two of us interested in researching the dark web: In Spring 2017, I (Brady) was looking to purchase a car from one of the popular used car dealers. After scrolling through the dealer’s website for thirty minutes, I closed this tab and opened a new one to visit my favorite news site. I was surprised to find, about a third of the way down the page, an ad for the exact cars I was looking at earlier from the same dealer whose site I was on (plus two other dealers!). I never consented to letting my browsing behavior be tracked from site to site. I definitely did not consent to them also sending an email to the account I was logged into during my browsing. Some might call this convenience (at least your ads are relevant)—I consider it an invasion and, at the very least, creepy for the implications this data collection could one day have.So I began to seek ways in which to avoid this kind of tracking—finding a potential answer in the dark web, that “insidious technology” that I had previously only heard berated in popular culture. I was surprised, in reading more about it, what this technology was designed for and what it could offer in the way of privacy, not just in my case with the ads, but also for individuals around the world facing censorship (either ofthe Internet or ofthought). This is the side ofthe dark web we want you to hear about.
I met Matt shortly after the 2017 American Library Association Annual Conference in Chicago, where I did a short presentation on the dark web and the need to research it further as a privacy technology. Matt brings the information systems background to pair with my social science background. He brings the perspective o fan information worker and a PhD student/thinker (who tries, and fails, he says, to channel the writing of James Gleick and John Budd). We both bring a level of wit and humor that, at least in my case, is probably inspired by reading too many Stephen King books and listening to Eminem and The Clash as a teenager. Together we quickly began the project that would become the book you are reading now.
We have structured the text so that the chapters both build on one another and can be read in isolation. That means you can read it front to back and it will read as a complete story, or you can use it as a reference and flip around. The book also has theoretical aspects (well, kind of—not enough to bore you) and technical aspects (how to install and use the technology), but it focuses primarily on telling you what things are in a simple, approachable manner. In our minds, there are three natural divisions in the book: chapters 1–4 describe what the dark web is, its history, how it works; chapters 5–6 provide information on how to access the dark web and an index of sites to explore (with clear demarcations between sites that we recommend and those that have questionable content); and chapters 7–9 deal with issues and opportunities with the dark web and some big picture philosophical thinking. We have tried to create clear and descriptive chapter titles, but will also discuss briefly the content of each chapter here.
As an Amazon Associate I earn from qualifying purchases.
With this book we assume that all of our readers know absolutely nothing about the dark web. It is okay if you do—we think you will still get a lot out of this book—but we always hate books that start just one level above where we are, so that we kind of get it, but not really. By assuming you know nothing, we hope this problem is eliminated.
Chapter 1, then, is simply titled "What Is the Dark Web?" If we were going to record a twenty-minute PSA for the general public on YouTube, this is what we would say you should know about the dark web. Chapter 1 also gives you a taste of our writing style, which will hopefully get you through some of the more information-intense/technical aspects ofthe dark web we discuss.
Chapter 2 is not directly a history of the dark web, nor is it a history of the people who use the dark web. Like we said earlier in this preface, we could give you a hall of fame of whistleblowers who demonstrate the need for the dark web, but that detracts from the overall aim of this book. If you are interested in a book about whistleblowers, there are many great ones out there, but this is not one. This history instead focuses on how the dark web is even possible. We discuss information theory, computer science, the Internet, and dark web technology. The goal is to give you a respect for the history of all these technological developments and how we view the dark web as a step in the progression of advancement.
Chapter 3 gets into deep detail about how the dark web works. Trust us, it is worth reading, even if it is technical—and it gets easier from there.
Chapter 4 is written to be conversational, like a Q&A. Here we have a list of myths about the dark web and how we would respond to them. We also mention the dark web scans that you hear about on TV and whether they actually do what they say they do.
Browsing the Dark Web
Chapter 5 is your guide to installing the three major dark web platforms: Tor, Freenet, and I2P. Tor is the platform that is typically referred to when one talks about the dark web, but all three we discuss here have a good deal of popularity. Much of the information in the early part of this chapter is available on the sites of the individual platforms, and we encourage you to visit these sites to read more about the three platforms. The second part of the chapter discusses the similarities and differences between the platforms and addresses some questions about which platform is right for you.Unfriendly Dark Web
Chapter 6 aims to help address a major challenge for the dark web platforms: lack of a search engine. In addition to a history of dark web sites, we provide an extensive index of these sites with information about them and guidance about whether we would recommend visiting the site to our minister.Intellectual dark web
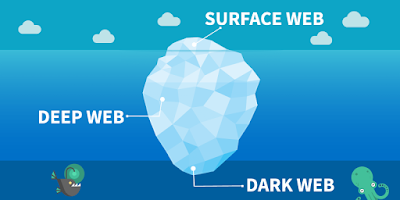
Chapter 7 dives deeper into the legal and ethical considerations with the dark web. We talk about the history of illegal activity on the dark web and distinguish between the positive and unsavory aspects ofthe dark web.Dark web vs deep web
Chapter 8 is our attempt to further the discussion about the dark web. If our book moves you to explore the dark web further, or work to support it, chapter 8 will give you some guidance on how to do so. We appeal to the spirits of Everett Rogers and Thomas Kuhn to raise the true dark web into the public consciousness. (If you do not know who those two are, consider yourself lucky you did not have to take a semester-long course on them, but also read up on them because, hey, they are the most influential social theorists of the twentieth century.) We also discuss the untapped potential for legitimate commercial ventures on the dark web.Is the dark web illegal?
Chapter 9 ties everything together with the surprisingly similar stories of how the Internet was viewed in the early 1990s and the dark web is viewed today. It is a gem of the Internet Archive that we hope will leave you thinking and wanting to investigate the dark web further.How to use dark web?
Writing Casting Light on the Dark Web was a passion. We hope that this book establishes a greater discussion of the dark web in the global society. It does not really matter what side of the issue you come down on; what matters is that we talk about the dark web while we have the opportunity and do not let it fall to obscurity or get completely overrun by illegal content that forever tarnishes its potential to bring benefit to the world. So give this book a read and then let someone else have a read and talk about it. Let’s start a critical discourse about whether we should protect this technology, police it, or allow it fall to obscurity. Do not let time decide for us!Download: Casting Light on the Dark Web the perfect book to browse safe

Comments
Post a Comment